
Bridging the Gap
The Differences and Synergies Between the Vehicle Security Operations Center (VSOC) and the Product Security Incident Response Team (PSIRT)
This white paper describes two critical components of modern cybersecurity in the automotive ecosystem: the Vehicle Security Operations Center (VSOC) and the Product Security Incident Response Team (PSIRT). It provides detailed definitions, highlights key features, and outlines the core functions for each entity. It also evaluates how these capabilities are typically adopted across the supply chain from automotive manufacturers (OEM) to their suppliers. Finally, the document explores overlapping areas and collaboration opportunities between VSOC and PSIRT, offering guidance on aligning operational security with product vulnerability management to lower costs and strengthen overall cybersecurity posture for customers.
Introduction
Connectivity now reaches every corner of the modern vehicle. The infrastructure enabling the features consumers demand–like over-the-air updates, telematics APIs, dealer diagnostic links, and in-car app stores–broaden the attack surface. Attackers capitalize on dormant design flaws that are challenging to identify during development and may hide for years before triggering warranty claims, recalls, or safety incidents. In 2023, software defects drove roughly 23 percent of all U.S. vehicle recalls. To stay ahead of fast-moving exploits and long-dormant vulnerabilities alike, the industry leans on two specialized cybersecurity capabilities:
- VSOC (Vehicle Security Operations Center): a dedicated operations center that monitors the rolling fleet and responds to anomalies or policy violations.
- PSIRT (Product Security Incident Response Team): a team and set of tools/processes that manages vulnerabilities in software and hardware components throughout the product life cycle.
Overview of VSOC
Definition
A VSOC is a specialized security operations center designed to monitor, analyze, and respond to cybersecurity incidents within the automotive ecosystem. Unlike traditional SOCs that focus on IT or network infrastructures, VSOCs address the unique challenges of vehicular communication networks and connected systems and depend on automotive-specific use cases that vary by vehicle brand and model. Figure 1 illustrates a high-level flow of data and functions within a VSOC.
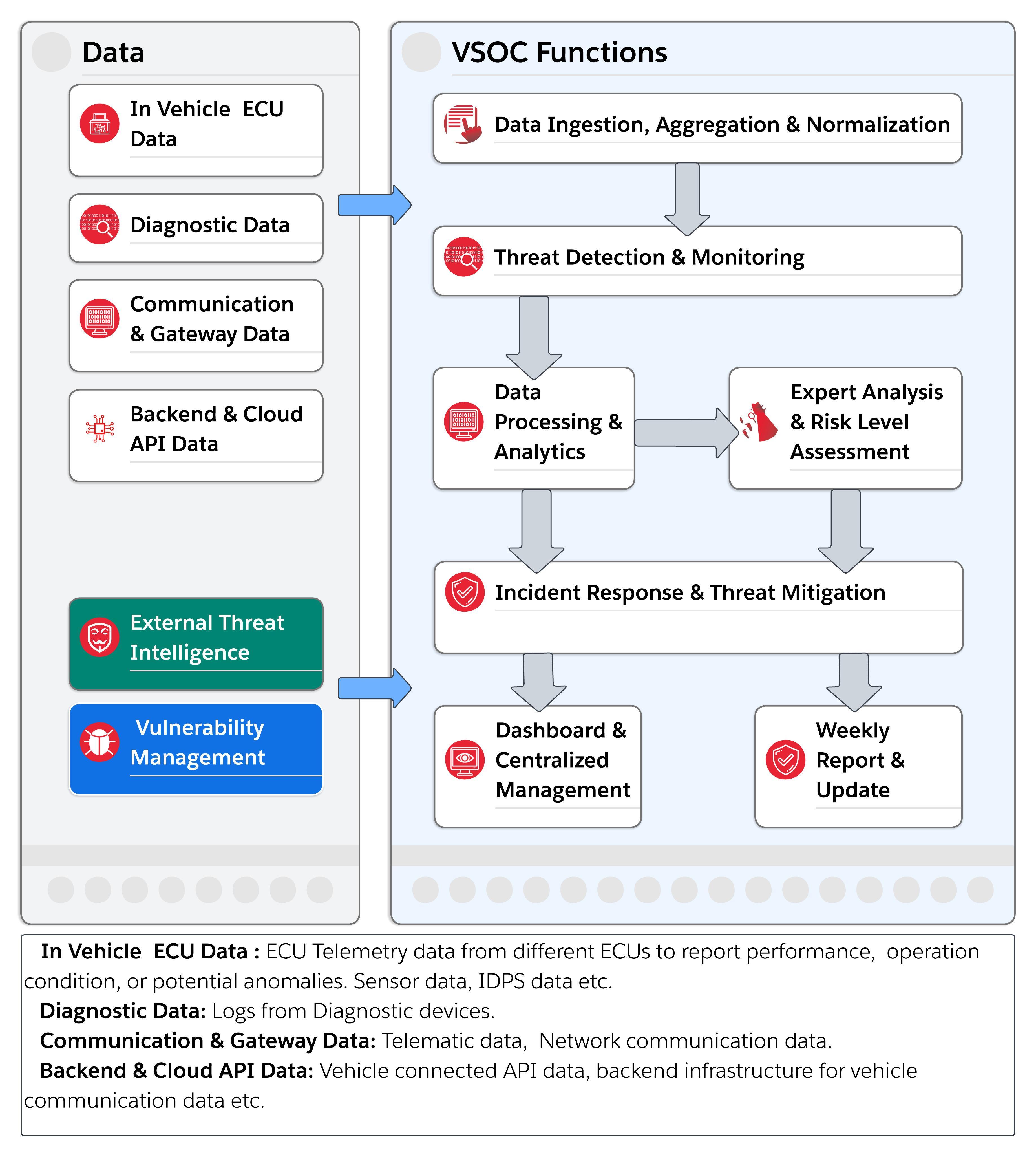
Key Features
- Continuous Monitoring
The VSOC continuously monitors various vehicle networks such as telematics systems, diagnostic systems, and other vehicle communication systems, keeping a constant check on the data flowing through these systems. This continuous monitoring means that any unusual activity or predefined trigger—such as a deviation from normal behavior or installing an odometer blocking device—is detected and handled appropriately. An important point to note is that “continuous monitoring” is not necessarily “real-time” nor “24/7”. Neither UN R155, ISO/SAE 21434, nor NIST SP 800-137 (Information Security Continuous
Monitoring (ISCM) for Federal Information Systems and Organizations) define a set cadence, but monitoring should be sufficient to support risk-based decisions.
- Automotive-Specific Threat Intelligence
The VSOC collects and integrates threat information that is specific to the automotive world. This means they keep track of vulnerabilities and risks that are unique to the systems within vehicles, including those found in traditional in-vehicle networks and the newer vehicle-to-everything (V2X) technologies. By having up-to-date, specialized threat intelligence, a VSOC’s security measures are always aligned with the latest challenges facing modern vehicles.
- Data Ingestion Pipeline
The VSOC collects and consolidates information from diverse sources: onboard sensors, electronic control units (ECUs), telematics modules, log uploads, and cloud‐stored data. Most is funneled into a centralized analysis platform, ensuring every relevant data stream is available for security monitoring and investigation.
- Custom Dashboards
The dashboards display the vehicle’s security status through a combination of point-in-time snapshots and incident-driven alerts. These dashboards bring together all the important data in one place, using clear visuals and interactive elements to help security teams quickly understand what’s going on. Whether it’s tracking incident alerts or reviewing trends over time, the dashboards offer a straightforward way to stay informed and take necessary actions when needed.
Core Functions
- Incident Detection & Response
Analytics and rules flag deviations from normal vehicle behavior or triggers from pre-defined use-cases; analysts confirm the alert and launch automated or manual playbooks and escalate issues to PSIRT / engineering when needed. - Collaborative Operations
The VSOC shares live indicators with automakers, suppliers, and regulators and ingests their advisories in return. This two-way flow unifies threat coverage across the ecosystem and ensures that fleet telemetry, threat-intel context, and policy requirements all inform the same security picture. - Operational Forensic Investigation
After containment, analysts secure logs, telemetry, and memory images to rebuild the attack timeline. This “first-mile” forensics explains what happened and feeds fresh indicators to detection rules, while the packaged evidence moves to PSIRT / engineering for deeper product-level root-cause analysis. - Reporting & Continuous Improvement
Each incident feeds dashboards that track mean-time-to-detect, containment effectiveness, and recurring attack techniques. Regular post-mortems turn those insights into updated playbooks, tuned analytics, and targeted staff training, so the VSOC responds faster and more accurately with every event.
Overview of PSIRT
Definition
A Product Security Incident Response Team (PSIRT) is responsible for the identification, assessment and disposition of product security risks over the product’s lifecycle. In the automotive context, the PSIRT focuses on addressing software and hardware flaws that could compromise the safety, reliability, privacy, or cause financial impact of compromised vehicle systems. Figure 2 shows how the PSIRT lifecycle processes interact with other functions/teams in each of the states.
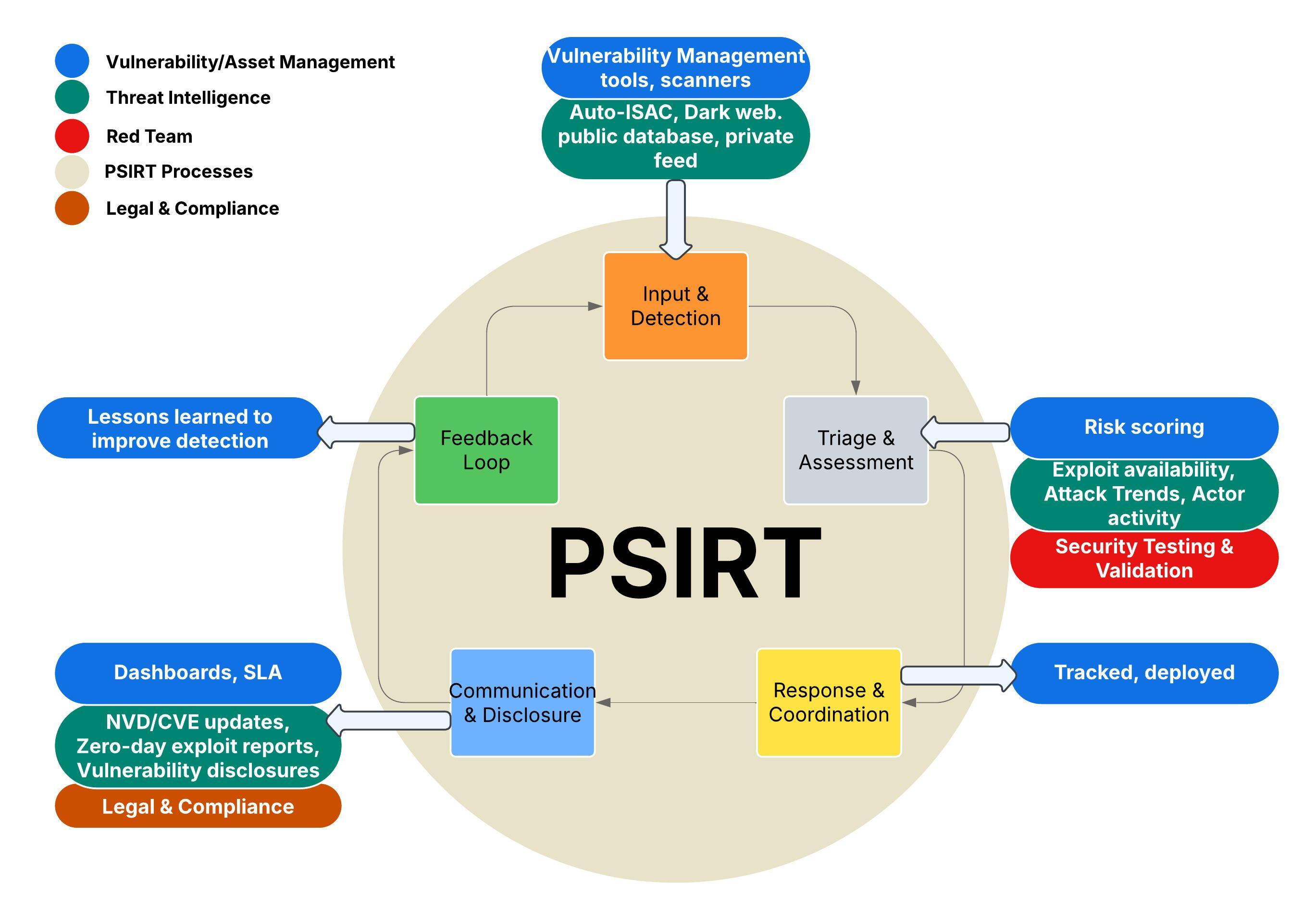
Throughout the PSIRT lifecycle, key functions such as vulnerability and asset management, threat intelligence, security testing, and compliance provide essential support and guidance.
Key Features
- Structured but Flexible Intake
The PSIRT ingests a variety of data sources including SBOMs, HBOMs, TARAs and information from suppliers; responsible disclosure program inputs; security assessments; and the VSOC. It must then cross-reference this data with NVD, Auto-ISAC feeds, and other product vulnerability sources to determine potential risks affecting specific products.
- Cross-Functional Collaboration
PSIRT emphasizes close coordination among various teams—engineering, quality assurance, legal, supply chain, and customer support—to address vulnerabilities effectively. This collaborative framework allows technical experts to work alongside those who understand product quality and customer impact, ensuring that vulnerabilities are not only fixed quickly but also prioritized accordingly.
- Stakeholder Communication
From immediate alerts at the time of discovery to detailed reports and updates during the resolution process, the goal is to ensure that all stakeholders understand what happened, what actions are being taken, and how future incidents will be prevented.
- Proactive Vulnerability Management
The vulnerability management is proactive rather than reactive. PSIRT’s goal is to prevent VSOC incidents by analyzing product risk–accounting for both up and down stream supply chain effects–making risk determinations, issuing Vulnerability-Exploitability eXchange (VEX) statements, and helping to prioritize remediation with engineering teams.
Core Functions
- Vulnerability Oversight:
From first report to final closure, PSIRT provides a governed path that documents scope, impact, and ownership—supporting auditability and executive visibility.
- Remediation Orchestration
The team aligns software, hardware, and cloud changes into coherent delivery packages, verifies them on target platforms, and ensures phased roll-outs to minimize customer disruption.
- Risk Containment
When permanent fixes require long lead times, the PSIRT prescribes compensating controls—such as enhanced VSOC monitoring or configuration hardening—to shrink exposure windows without compromising safety or compliance.
- Continuous Learning & Outreach
Post-incident reviews, trend analyses, and knowledge-sharing sessions convert lessons learned into updated engineering standards and supplier requirements, ensuring the next product generation starts from a stronger security posture.
Comparative Analysis and Overlap
The VSOC focuses on the operational aspects of vehicle security. It is designed to monitor continuous data streams, detect intrusions or anomalies in the vehicular environment, and respond reactively to new threats which were previously either unknown or lower priority. The PSIRT concentrates on the lifecycle management of product security and proactively preventing VSOC incidents. This includes managing vulnerabilities from discovery to remediation and ensuring that products are secure from design through post-deployment.
There are overlapping areas between PSIRT and VSOC and both teams rely on shared threat-intelligence and vulnerability-management systems to coordinate a single, evidence-based response. The following table lists the integration opportunities between VSOC and PSIRT
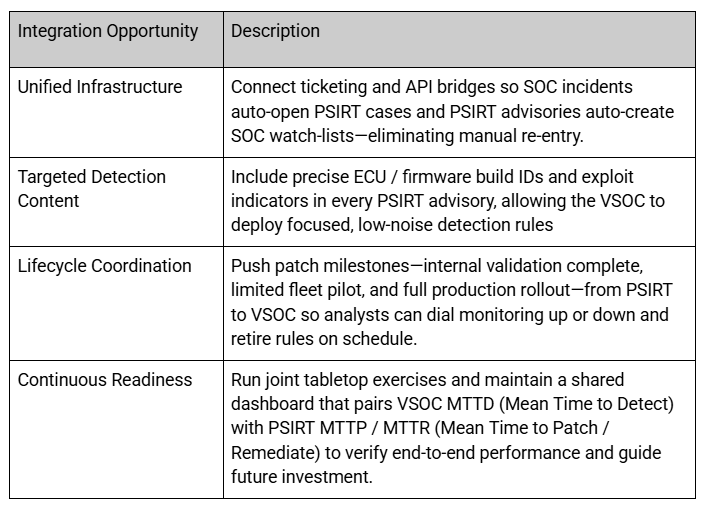
Information Sharing & Team Enablement
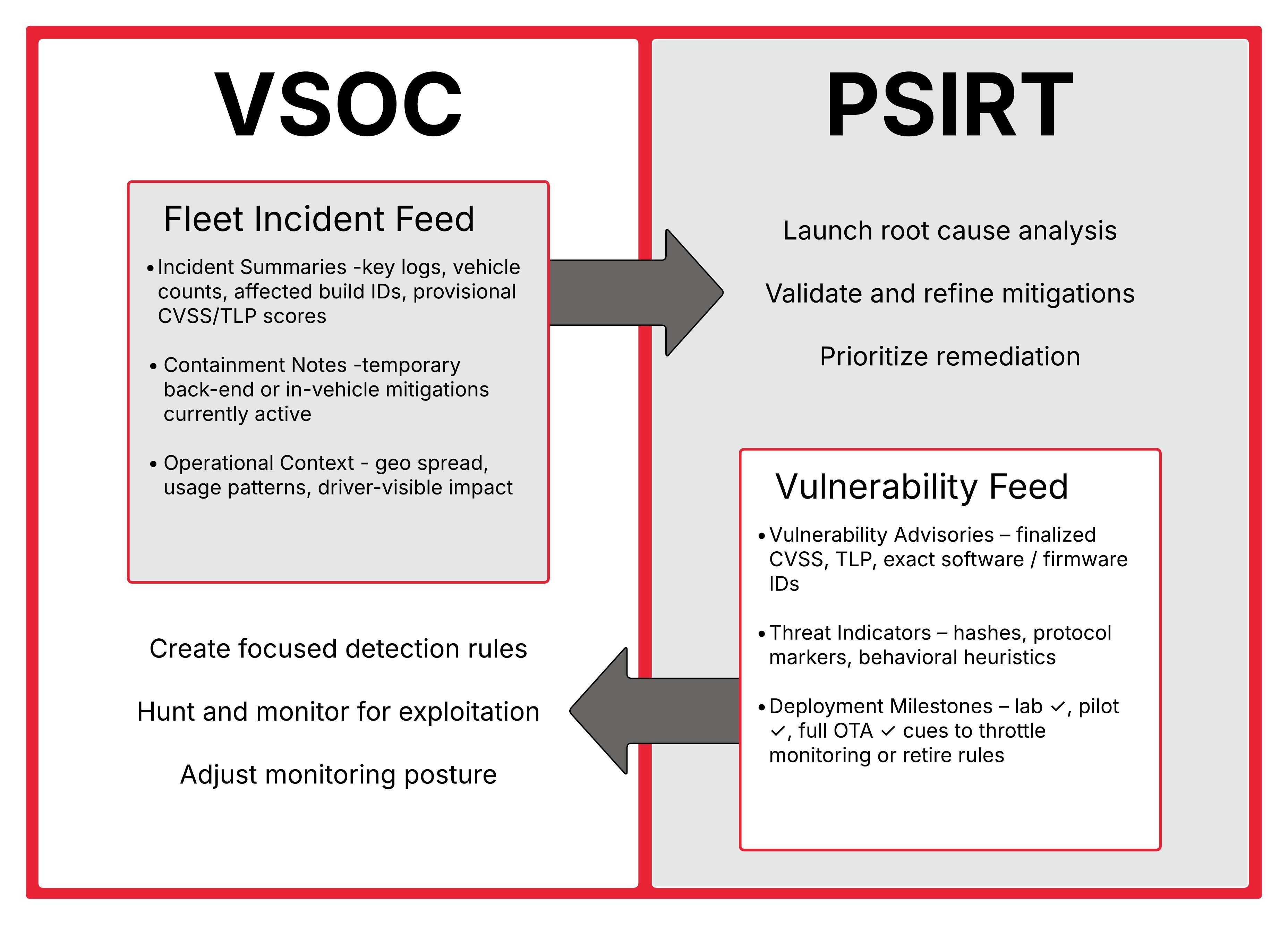
Efficient collaboration hinges on a small, clearly defined set of data exchanges. The lists below outline what the VSOC sends to PSIRT—and what PSIRT returns—so each side can act without delay and without duplicate effort. Figure 3 illustrates information sharing opportunities across the teams and potential resulting activities.
VSOC → PSIRT
- Incident summaries – logs, vehicle counts, affected build IDs, and provisional severity (CVSS/TLP) are forwarded so product teams can begin root-cause work without waiting for a formal post-mortem.
- Containment notes – any temporary actions taken in the backend or at the vehicle (for example, disabling a service or tightening request thresholds) are recorded; PSIRT knows which mitigations are in force while a patch is prepared.
- Operational context – geographic spread, usage patterns, and driver‐visible impact help PSIRT prioritize fixes that carry the greatest business or safety risk.
PSIRT → VSOC
- Vulnerability advisories – confirmed issues are returned with final CVSS scores, TLP labels, and exact software/firmware identifiers, allowing the SOC to create focused detection rules.
- Threat indicators – hashes, protocol markers, or behavioral heuristics derived during analysis arm the VSOC to spot exploitation attempts during staged roll-outs.
- Deployment milestones – as patches clear lab, pilot, and full OTA release, PSIRT signals each phase so SOC analysts can dial monitoring up or down and retire rules on schedule.
Why it matters
Using shared constructs—CVSS for severity, TLP for information-sharing boundaries, software build IDs for precision—keeps the hand-off lightweight and audit-ready. Fleet observations reach the engineers who own the code, while newly scored vulnerabilities harden fleet monitoring before attackers have a chance, giving both OEMs and suppliers a clearer, faster path from detection to durable fix.
Case Studies / Use Cases - VSOC and PSIRT Collaboration
The following scenarios translate the earlier concepts into practical outcomes, showing how a Vehicle SOC and a PSIRT work together under real operating conditions. Each case highlights a different trigger—live intrusion, lab-found vulnerability, and day-to-day operations—and traces the hand-offs that convert raw data into a fleet-wide fix.
Case Study 1: Real-Time Incident Response
An automotive manufacturer detected abnormal behavior in its vehicle’s telematics system. The VSOC quickly identified a potential intrusion and activated a coordinated response with the PSIRT. While the VSOC managed the immediate threat containment, the PSIRT conducted a comprehensive vulnerability assessment, and–coordinating with suppliers–implemented a patch across affected models. This approach minimized downtime and protected customer data.
Case Study 2: Proactive Vulnerability Mitigation
A vulnerability was discovered in a vehicle infotainment system during routine testing. The alert, triggered by the Testing team’s finding, notified the PSIRT team who initiated a vulnerability analysis and developed a remediation plan. Simultaneously, the VSOC monitored for any exploitation attempts, ensuring that no active threats emerged. The collaboration resulted in a timely patch release and reinforced the product’s security integrity.
Use Case: Integration of Monitoring and Response
By integrating VSOC’s real-time monitoring capabilities with PSIRT’s structured incident management processes, an organization can build a feedback loop. This loop enables continuous improvement in threat detection, rapid response, and more efficient vulnerability management. Such integration not only reduces response times but shifts operational budget towards proactive remediation, reduces the flow of data through expensive SIEM systems, and strengthens the overall security posture of the product and operational environments.
Conclusion
This white paper has illustrated the substantial benefits of employing specialized cybersecurity strategies for the automotive ecosystem. On one hand, a dedicated security operations center that delivers expert, around-the-clock monitoring, rapid detection, and immediate incident response is crucial for safeguarding operational environments. On the other hand, a comprehensive product security incident response system effectively manages vulnerabilities — conducting continuous scanning, risk assessment, and coordinated patch management — to ensure products remain secure throughout their lifecycle.
These approaches can be deployed independently to address specific security needs or integrated to create a unified defense that leverages the strengths of both real-time threat monitoring and systematic vulnerability management. Whether adopted separately or together, each strategy offers a focused, robust safeguard against the ever-evolving landscape of cyber threats in the automotive sector.
Stay Connected with Block Harbor
Keep up with the latest in vehicle cybersecurity through our specialized newsletters. Choose the option that best fits your interests and role.
Thank you for your submission!
Read More
Explore more automotive cybersecurity insights from our experts. Discover best practices, case studies, and emerging trends to strengthen your organization's security posture.

A quick guide to using a structured Medical Device Cybersecurity Checklist for safer, compliant connected devices.
The state of automotive cybersecurity today and the forces that will define what comes next.

Announcement of Block Harbor’s selection for the Google AI Academy: American Infrastructure, highlighting our mission to secure AI-powered mobility systems like connected vehicles, drones, and robots through the VSEC cybersecurity platform.
Try Block Harbor Today
Start protecting your vehicles with the same platform the world’s best hackers and defenders use.


%201.svg)




